A secure VPN is one of the most important aspects of your company's network security. So how do you balance your employees' remote access with the risks of inadvertent data breaches, leaks and hacks? One solution many organizations are adopting is a Zero-Trust network architecture.
We'll explore how with the right tools in place, VPNs and Zero-Trust Networks can happily coexist. This means you can take all the necessary precautions to protect your internal network, while also providing staff with a secure yet user-friendly solution to get connected and work productively.
Discover VPN Tracker
VPN Tracker is a sophisticated VPN client solution, offering organisations multi-protocol VPN support for macOS and iOS systems. Roll out preconfigured VPN connections and shortcuts to staff using secure end-to-end encryption.Get started with VPN Tracker →
What is a Zero-Trust network policy?
With a Zero-Trust network policy in place, access to the company network is completely restricted for every user - including users who are on the premises. In order to access company resources, users need to go through a strict authentication process, which is intended as a solution to stop security breaches and ensure access is kept secure.
Three of the main principles of Zero-Trust are:
- User / application authentication
- Device authentication
- Granting least privilege access
Despite its security strengths, compared to a standard VPN, a Zero-Trust policy is much more difficult and time-consuming to set up and manage. However, your existing VPN can also be optimized to integrate many of the key Zero-Trust characteristics and offer your company network more security.
How to make your Company VPN more secure
If you are looking into adopting a Zero-Trust policy into your current network structure, here are a few key steps you can take to protect your organization from threat and make your connections more secure.
Harden your VPN connection
The first step for securing your connection is ensuring your VPN has the optimal security settings in place to protect the network from external threats.
To begin with, you should start by reviewing your VPN's encryption settings. Are you using the highest encryption algorithms supported by your gateway? VPN Tracker supports encryption up to AES-256 to satisfy even the most demanding standards set by military organizations, enterprises and government.
We also recommend not using MD5 as a hash algorithm and to choose SHA-2 whenever possible. In addition, you should consider using a high DH group and enabling PFS in Phase 2 (if supported by your gateway.)
Choose a secure VPN client
The VPN app on your users' devices is the gateway into your company's network, so it needs to be kept as secure as possible. In general, all security relevant software should be checked and vetted to see if they support best practises.
A good VPN client should offer you:
- Secure, end-to-end encryption standards for your connection data (learn more)
- Custom configuration options for connections
- Trustworthy and reputable developers
- Regular maintenance and updates. VPN client software which is not regularly updated can leave your business open to threats, i.e. when it is not compatible with the latest security patch updates or doesn't offer support for the latest technologies
For Mac, iPhone and iPad users, VPN Tracker is the top choice VPN client and offers full compatibility with the latest macOS and iOS versions.
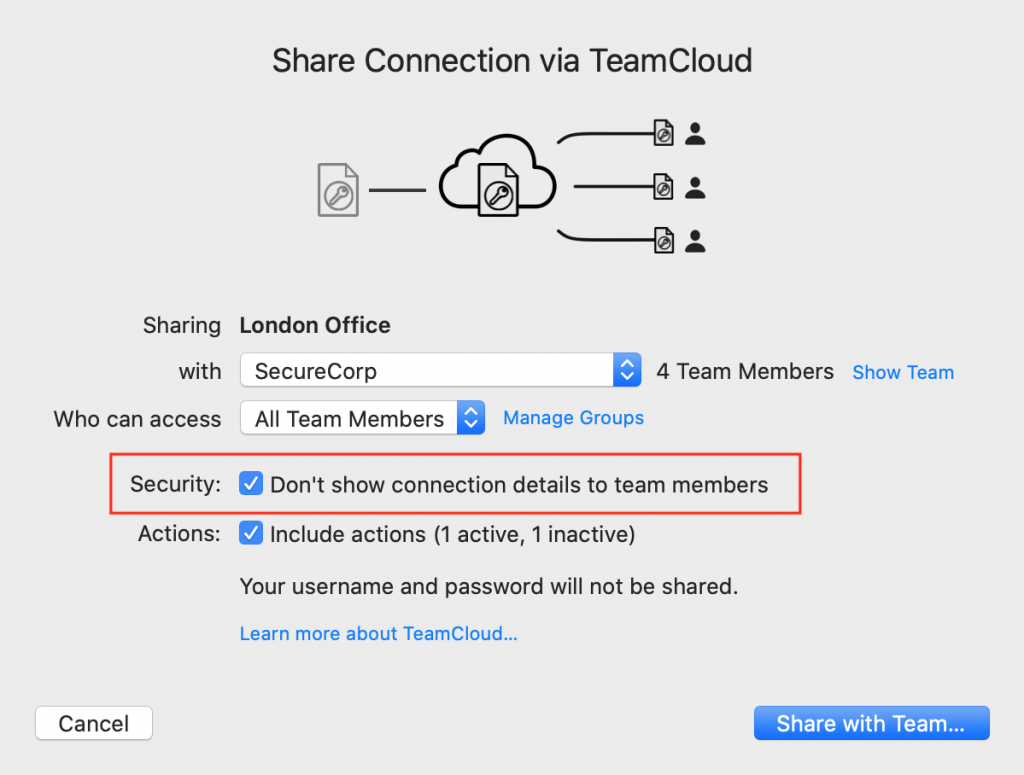
Phishing countermeasures - hide connection details from users
Social engineering or phishing attacks only work if employees have access to sensitive data, such as your connection's Pre-Shared Key or Shared Secret, or even the VPN gateway address or VPN protocol in use.
Hiding this information before you share the connection is one extra way of eliminating risk.
In addition, by hiding connection details from VPN users, you can also ensure they have no way of using your connections with other external, untrusted software - a key concept within Zero-Trust security.
With VPN Tracker TeamCloud, you can securely share pre-configured VPN connections with team members and hide all the connection details before export:
Verify users with Two-Factor-Authentication
Having a secure user verification process in place is another key part of building an effective Zero-Trust network. When sharing information with individuals within your organisation, you need to be sure that the identity of the person receiving the information is legitimate.
Two-Factor Authentication (2FA) is on the rise and is already built into many leading VPN services. With 2FA in place, your VPN has another layer of protection against hackers and cyber attacks, such as email phishing or spear phishing.
VPN Tracker offers support for for two-factor authentication (2FA, MFA, OTP) based on X.509 certificates, OTP authenticator apps like Google Authenticator, Duo etc. or smart cards, and PKI tokens. Hardware-based one-time passcode tokens and hardware security tokens such as YubiKey, RSA SecurID, or FortiToken for FortiGate devices also work great with VPN Tracker through Extended Authentication (XAUTH).
Granting least privilege access
Another key principle of Zero-Trust security is only granting employees the minimum level of privileges. In other words, only giving users access to the connections they really need, in order to minimise potential risk and avoid unauthorised access to confidential information.
In VPN Tracker, this can be achieved using the Groups feature.
Set up TeamCloud Groups to grant pre-determined groups of users with access to specific VPN connections. This way, you can avoid giving users access to all of your company connections and instead only provide them with the resources they need to perform their tasks.
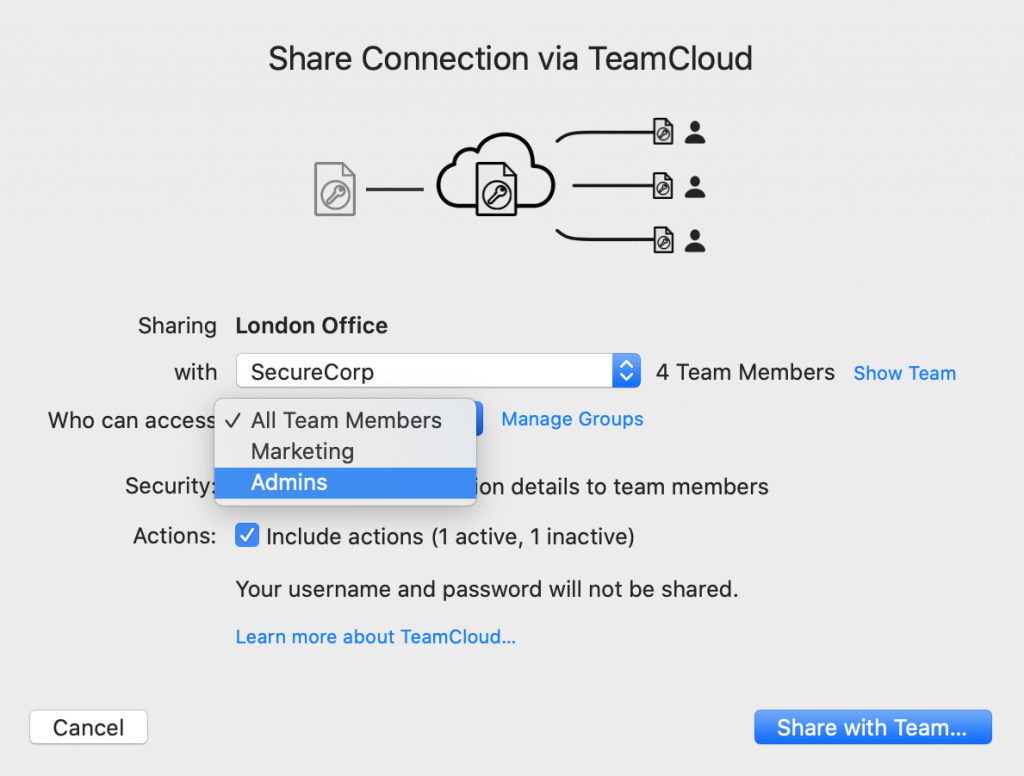
Set up Groups to grant and restrict access to connections
Why choose VPN Tracker for your organization?
VPN Tracker is the best VPN client for Mac, iPhone, and iPad, offering support for major VPN protocols, including IPsec, SonicWall SSL, SonicWall IPsec, Cisco AnyConnect SSL, Fortinet SSL, SSTP, and WireGuard®.
Your benefits with VPN Tracker
- Save time and securely deploy company VPN connections
- Centralized team management with managed connections, groups and notifications, and team audit logs
-
Compatibility with enterprise-level VPN gateways, including SonicWall, Cisco, Fortinet, and Sophos
- Zero-Trust compliant with role-based access controls
-
Advanced remote rollout with Configuration Profiles & Package Installer
- Unified billing for all users and dedicated "Billing" role for accounting purposes
- See all tech specs